
A network security audit is a comprehensive evaluation of an organization’s IT infrastructure, aiming to identify vulnerabilities, assess risks, and ensure compliance with security policies. This process involves scrutinizing various components, including hardware, software, network configurations, and user access controls, to detect potential weaknesses that could be exploited by cyber threats.
The audit typically begins with an inventory of all network devices and systems, documenting their configurations and current security measures. This step provides a baseline understanding of the network’s architecture and highlights areas that require attention. Subsequently, the audit examines firewall settings, ensuring that rules are appropriately defined to allow legitimate traffic while blocking unauthorized access. Regular reviews of firewall configurations are crucial, as outdated or misconfigured rules can create security gaps.
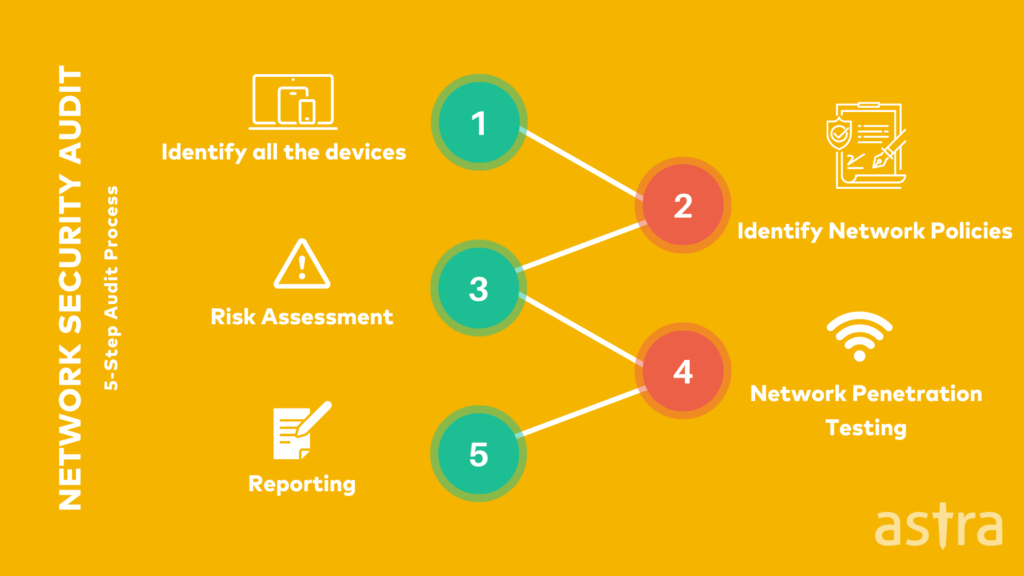
Access control policies are another critical focus area. The audit assesses user permissions to verify that individuals have access only to the resources necessary for their roles. This principle of least privilege minimizes the risk of internal threats and limits the potential impact of compromised accounts.
Traffic flow analysis is conducted to monitor data movement within the network. By analyzing traffic patterns, the audit can detect anomalies that may indicate malicious activities, such as data exfiltration or unauthorized communications. This analysis helps in identifying compromised systems and preventing data breaches.
The audit also evaluates the organization’s compliance with relevant security standards and regulations. Ensuring adherence to frameworks like ISO 27001 or GDPR is essential not only for legal compliance but also for maintaining customer trust and protecting sensitive information.
Upon completion, the audit provides a detailed report outlining identified vulnerabilities, their potential impact, and recommended remediation steps. This information enables organizations to prioritize security improvements and allocate resources effectively.
Regular network security audits are vital for maintaining a robust security posture. They offer insights into the effectiveness of existing controls, highlight areas for enhancement, and help in adapting to evolving cyber threats. By proactively identifying and addressing security issues, organizations can safeguard their assets, ensure business continuity, and uphold their reputation in an increasingly digital world.
In this article:
- Challenges in Network Security Audits
- 5 Pillars of Network Security Audits
- Essential Network Security Audit Best Practices

Challenges in Network Security Audits
Complex Network Topologies
Modern networks often span multiple locations, cloud services, and remote endpoints. Reviewing every segment, wired, wireless, and virtual, requires coordination among teams and clear visibility into each device and connection. Without accurate network maps, gaps can go unnoticed.
Evolving Threat Environment
New attack methods emerge daily, from IPv6 exploits to tunneled malware. Auditors must stay current on known vulnerabilities in routers, switches, and virtual appliances. Failing to update threat intelligence can leave critical risks unaddressed during assessments.
Resource Constraints
Smaller IT teams may lack dedicated staff or budget for comprehensive audits. Tight schedules and competing priorities can force rushed scans or skipped steps. Without adequate time and expertise, audits deliver only partial insights and leave blind spots in security controls.
Regulatory and Compliance Demands
Organizations must comply with standards such as PCI DSS, HIPAA, or GDPR. Auditors need to verify that network logging, segmentation, and encryption meet specific requirements. Keeping pace with shifting regulations adds extra workload and coordination with legal or compliance officers.
5 Pillars of Network Security Audits
Asset Discovery and Inventory
A complete inventory of routers, switches, firewalls, and wireless access points forms the foundation of any audit. Using automated discovery tools and manual checks ensures no device, on-premises or in the cloud, is overlooked. Accurate asset lists support consistent patching and configuration reviews.
Vulnerability Assessment
Scanning tools probe each network device for missing firmware updates, known exploits, and weak default credentials. By correlating scan results with threat feeds, auditors can rank vulnerabilities by severity. Prioritizing high-risk items, such as unpatched firewalls, helps reduce exposure quickly.
Configuration Review
Auditors compare device configurations against best-practice benchmarks (e.g., CIS benchmarks, vendor guides). Reviewing ACLs, NAT rules, and VPN settings helps spot misconfigurations that attackers could exploit. This step also verifies that password policies, SNMP settings, and SSH/Telnet access adhere to organizational standards.
Access Control Verification
Validating who has administrative rights on network infrastructure is critical. Auditors review user accounts, group memberships, and role-based access controls to ensure least privilege principles are enforced. Periodic review of service accounts and shared credentials helps prevent unauthorized access.
Incident Response Readiness
Beyond finding vulnerabilities, audits assess preparedness for a network incident. This includes reviewing logging capabilities, alerting thresholds, and escalation procedures. Testing incident response playbooks, such as simulated DDoS or lateral movement scenarios, reveals gaps in detection and containment processes.
Essential Network Security Audit Best Practices
Maintain Up-to-Date Network Diagrams
Accurate diagrams covering physical and virtual segments help auditors track data flows, identify choke points, and spot devices outside standard zones. Regularly update these diagrams as new switches or cloud subnets come online to ensure audits cover every asset.
Implement Continuous Monitoring
Rather than one-off assessments, integrate continuous monitoring tools that detect anomalous traffic, unauthorized configuration changes, and suspicious login attempts. Automated alerts keep security teams informed of new risks, reducing the window between vulnerability introduction and remediation.
Use Automated Scanning Tools
Leverage specialized network scanners that support SNMP, SSH, and API-based checks for routers, firewalls, and switches. Automated scans run faster than manual checks and provide consistent results. Schedule scans monthly or quarterly, depending on risk tolerance and change rates.
Enforce Strong Access Controls
Disable default accounts and change default credentials on all devices. Require multi-factor authentication for administrator logins to core routers and firewalls. Limit SSH access to trusted IP ranges and use certificate-based authentication where possible to prevent brute-force attacks.
Conduct Regular Follow-Up Audits
After remediation, schedule a re-audit to confirm vulnerabilities are truly resolved. Track open findings in a centralized ticketing system and assign clear ownership. Close the loop by verifying that patches applied correctly and configurations adhere to standards.







